How to Use the New Virtual Appointments in Microsoft Teams
Scheduling appointments is a common activity. Salespeople often set up virtual appointments to answer questions about a product. Software companies allow people to schedule live demos. Telehealth therapists allow clients to book video sessions.
Those are just a few examples of some groups that are going to love a new Microsoft Teams feature. Virtual Appointments was recently added to the platform. It adds a new meeting style tailored for engagements with customers.
Have you’ve been using Teams and a different online appointment app? This new feature will streamline the experience.
What Is Virtual Appointments in Teams?

Virtual Appointments gives you an all-in-one meeting platform for customer engagements. You can schedule, manage and conduct B2C meetings in Microsoft Teams.
This new feature brings together the scheduling component with the video conference interface. Anyone with the link can join the virtual appointment. They do not need a Teams account.
The power of Microsoft’s scheduling app, Bookings, connects to Teams. This makes the Virtual Appointments function as seamless as possible.
Some of the features below will be available with any Microsoft 365 plan. Some are available with a premium plan.
Teams Virtual Appointments Features
Manage Scheduled Appointments
You can see your scheduled appointments in a single view. Manage cancellations and time changes easily.
Send Customized Confirmations & Reminders
You can send customers a customized message via SMS or email. This personalizes the experience for them. You can also use automation to give that personal touch without having to send each one manually. Automated appointment reminders are another time-saving function.
Customized Waiting Room
Add a personal touch to your virtual engagements. You can customize the Teams waiting room. You can use themes and logos to brand your business. You can also chat with attendees while in the lobby waiting room. This is helpful if your current appointment is running a little long. You can let them know you’ll be right with them.
Meeting Follow-ups
You can send meeting follow-ups after a virtual appointment. This helps you reduce the time it takes to send any promised follow-up information. You also keep all details in a single place. This makes your client communication trail easier to follow.
Organization & Department Analytics
How effective are your appointments? It’s hard to know if your demos are resulting in sales if you don’t have a good tracking system. It’s also important to have visibility into customer appointments across the organization.
You can do this with a premium analytics feature. It gives you helpful reporting. The reporting provides insights into B2C virtual appointments in all departments.
How to Use Virtual Appointments
To start using Virtual Appointments in Teams, admins must set up a few things. Note, they must be a Bookings admin to access these settings.
Create a Calendar
In the Virtual Appointments app choose to “Create a calendar.” You can find this option on the Home tab.
Larger organizations may wish to create different calendars for different departments.
Add Staff
Next, add staff members. You can add up to 100. You will also need to assign them a role. Once you’ve added your staff, you can view their availability in both Teams and Outlook.
What’s another nice thing about using an integrated platform like M365? It’s the cross-app compatibility. Your calendar syncs across apps.
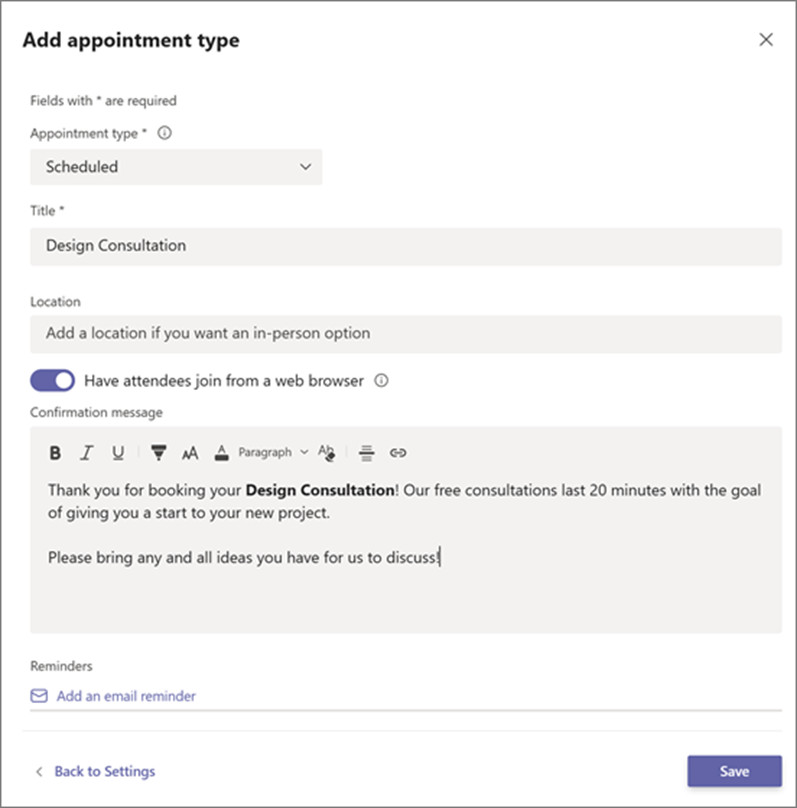
Create Appointment Types
You’ll next set up your appointment types. You can choose from these two options:
- Scheduled: You schedule the day/time. The system adds this information to the email confirmation.
- On-demand (Teams Premium): Customers can choose when to meet from your booking calendar.
Set Up SMS Notifications (If desired)
If you choose to use SMS notifications and have the right Teams plan, you can set this up next. This allows you to easily send appointment confirmations and reminders via text message. Note: Attendees currently need a valid U.S., Canadian, or U.K. phone number to receive the SMS notifications.
Link Forms (If desired)
If you would like your attendees to fill out any forms, you can link them now. Virtual Appointments allows linking up to four cloud-based forms. These would be forms you have created in Microsoft Forms.
Publish Your Booking Page
If you want to give customers the ability to book on-demand appointments, take this next step. You will need to publish the booking page. You do this on the “Manage” tab of Virtual Appointments. Select “Booking page,” and turn on “Publish booking page.”
Get Help Using Your Microsoft 365 Tools More Effectively
Microsoft 365 is a platform with many possibilities. Often, companies aren’t using all the features they could. As a result, their team may be less effective. They could also be wasting money on apps they don’t need.
Are you interested in help supercharging your Microsoft 365 experience? Give us a call today to set up a meeting.
Article used with permission from The Technology Press.